This guide will demonstrate the process of integrating a Kubernetes cluster with Keycloak for user authentication and authorization.
Requirements
- A running Kubernetes cluster
- Deployed Keycloak server
- The 2 servers can reach each others
Keycloak Setup
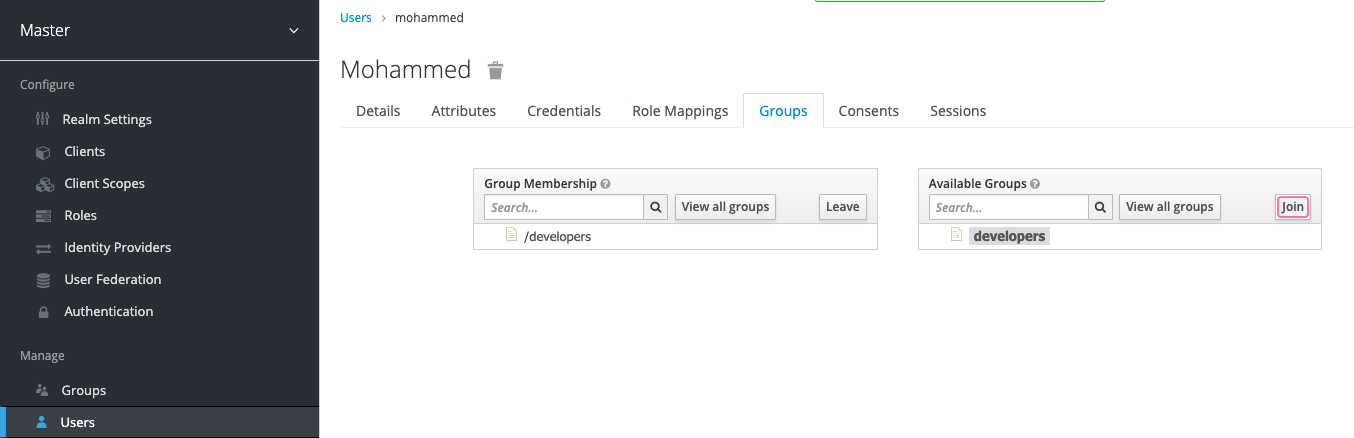
I will simply create a group called "developers", a user called "mohammed", then I will assign mohammed to that group to identify him as a developer.
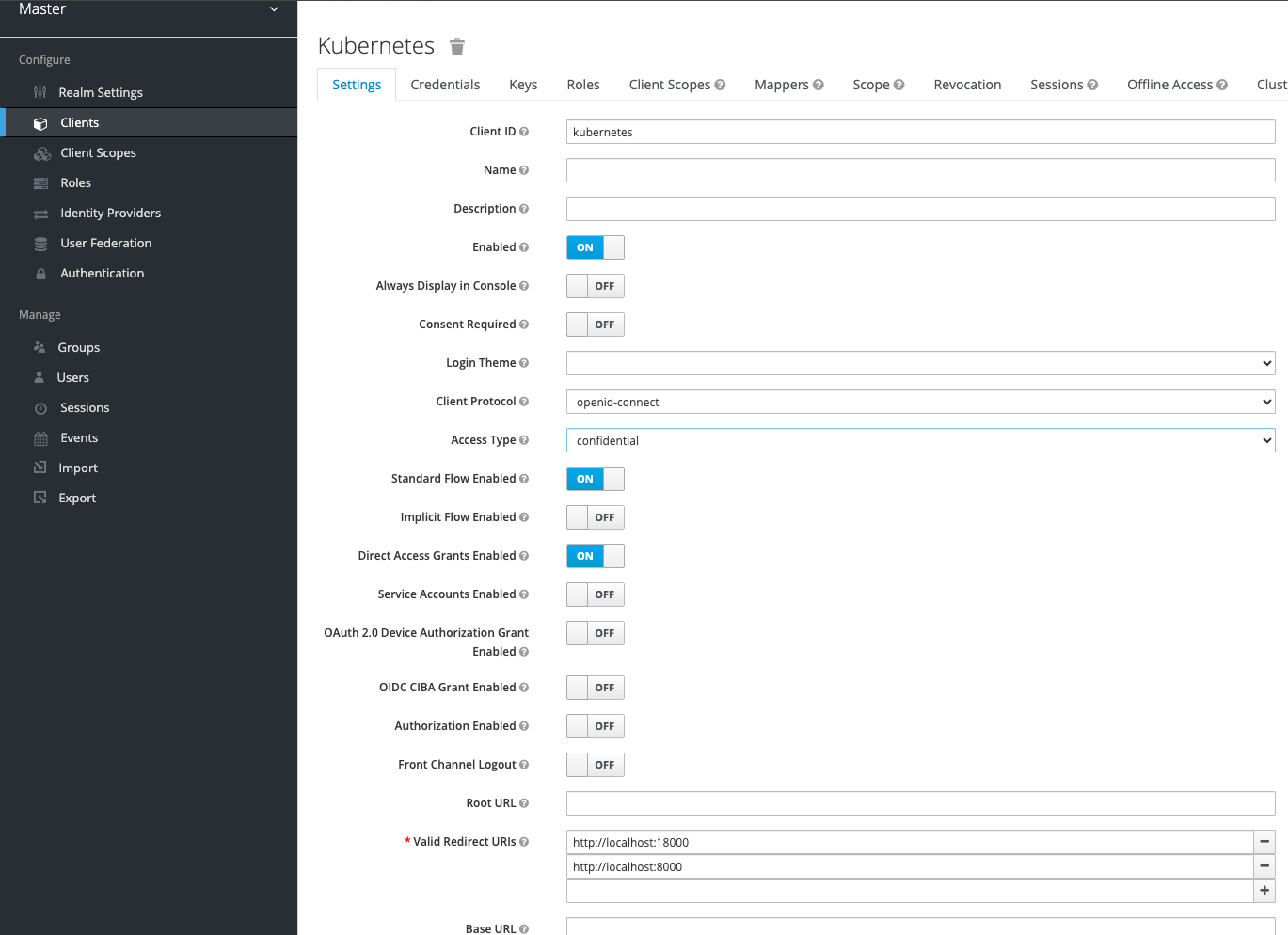
After that, I will create a client that Kubernetes would need to access to get the users. I will call this client 'Kubernetes'. Note: I will need the Client Secret from the tab Credentials for Kubernetes to access the client.
- Create Group and User
Create a group, for example "developers" that will contain all the users that are considered developers in Kubernetes context.
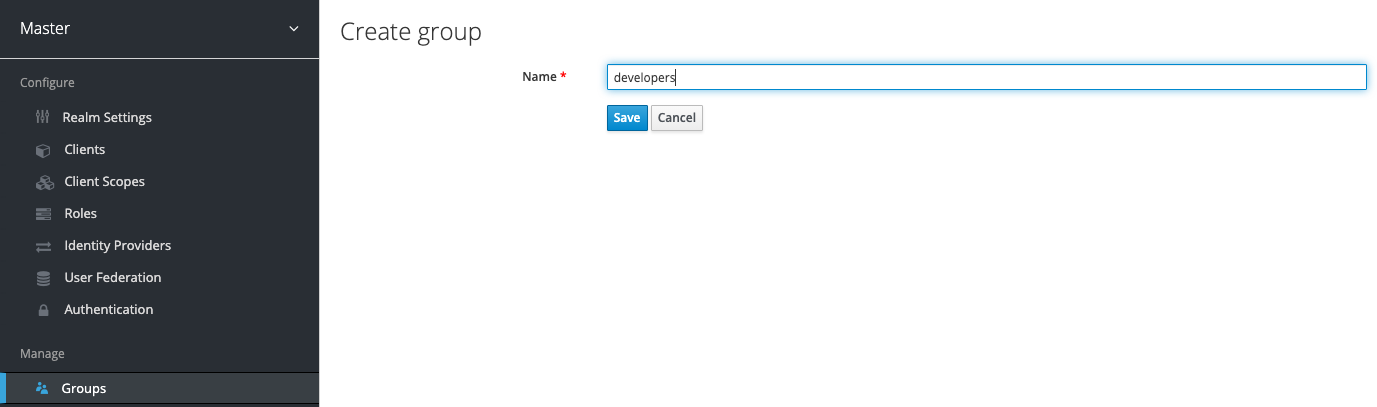
Add a user that will eventually be a Kubernetes user
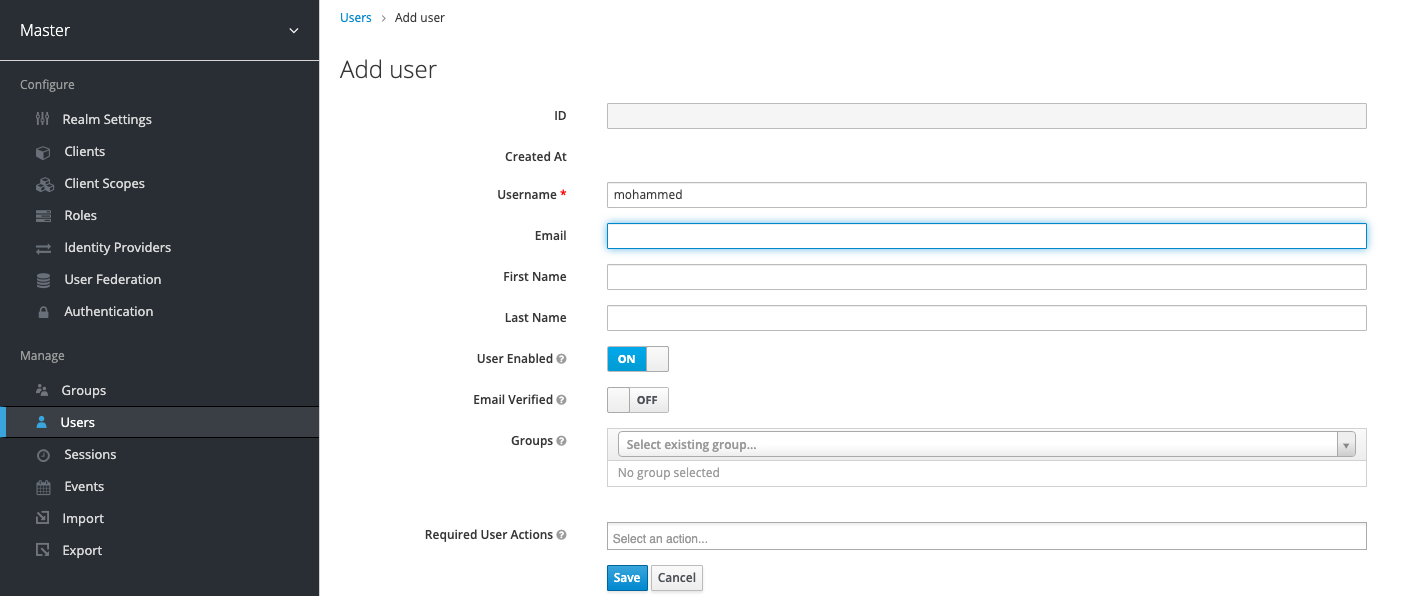
Create a password for the user from Users - Mohammed - Credentials.
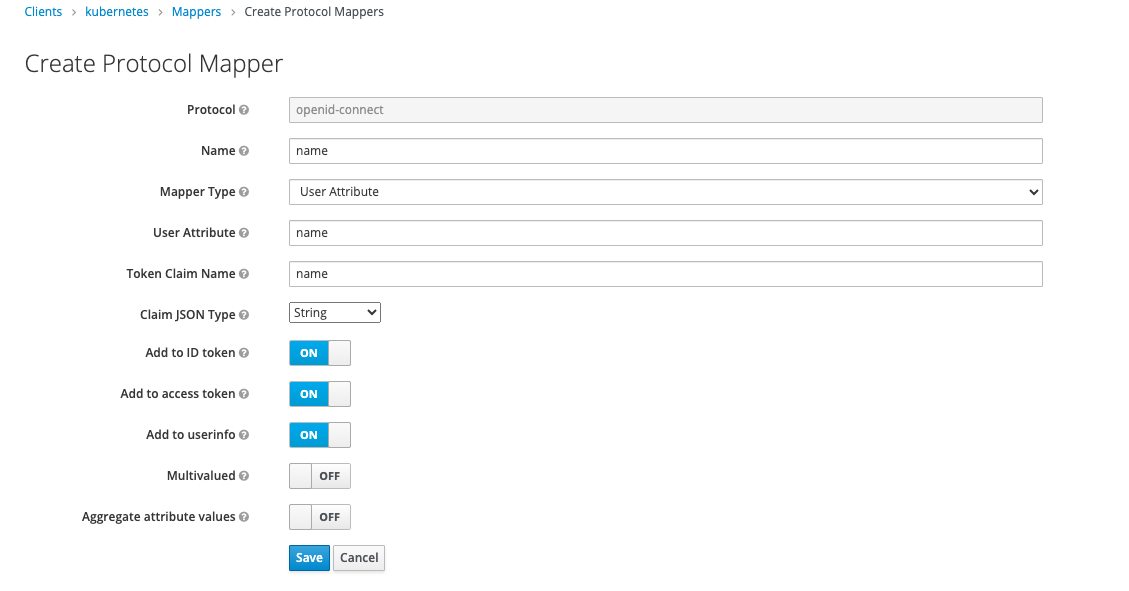
Then add a name attribute for that user
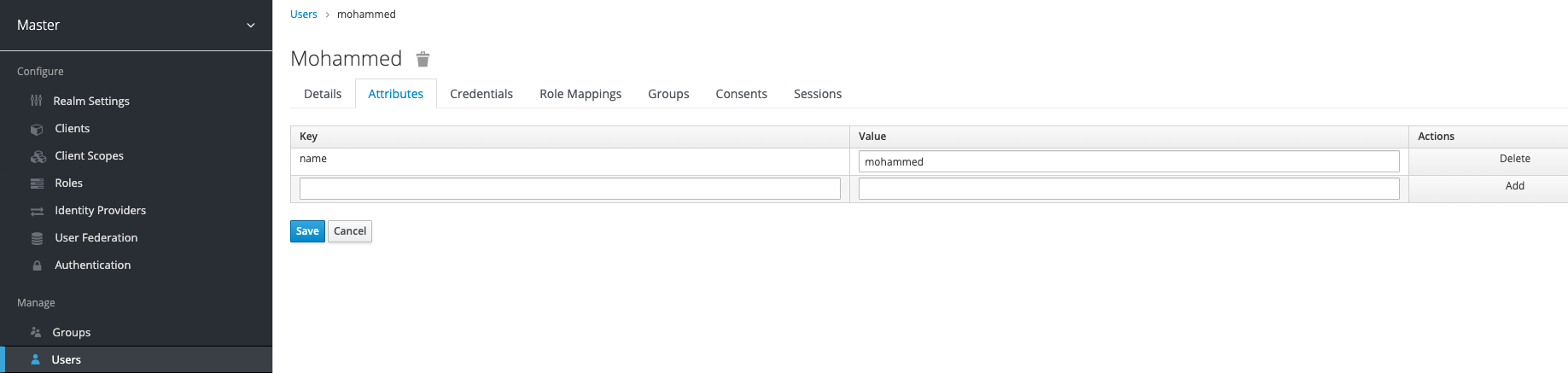
this attribute will be mapped into JWT.
Then, assign this user to the developers group
Finally, create a client from Clients - Create with the following configuration:
For this client, I have to add two mappers: name and groups:
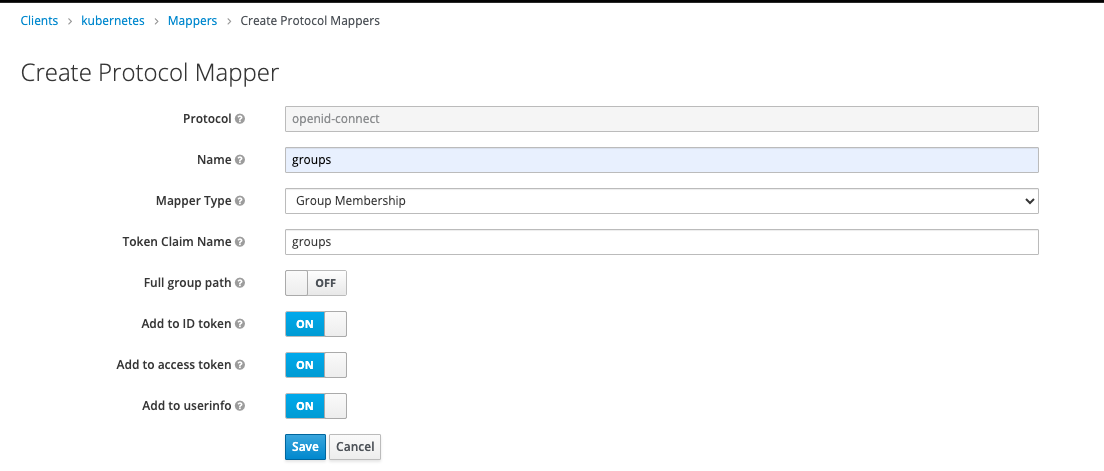
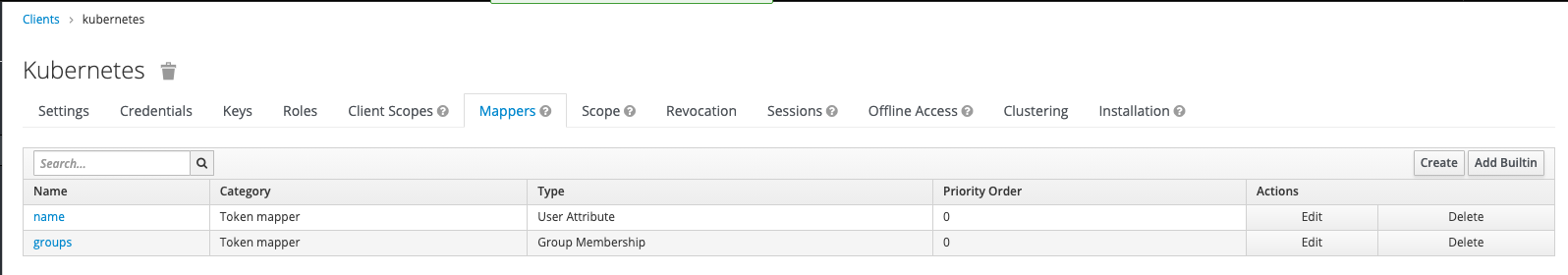
These mappers will inject the “Token Claim Name” as keys into JWT.
Remember the following properties configured to api server: (Next step)
— oidc-username-claim=name
— oidc-groups-claim=groups
I need to add some lines in the api-server yaml file. On the Kubernetes master, open the file:
nano /etc/kubernetes/manifests/kube-apiserver.yaml
Add these line
spec:
containers:
- command:
other configuration lines- --oidc-issuer-url=https://172.16.1.15:8443/auth/realms/master
- --oidc-client-id=Qjml0BljhnaLA2a203fYaVAU4GsZn5bt
- --oidc-ca-file=/etc/kubernetes/pki/rootCA.crt
- --oidc-username-claim=name
- --oidc-groups-claim=groups
- --oidc-client-id=kubernetes
In my case, Keycloak is running on https://172.16.1.15:8443.
oidc client ID can be found on Keycloak - Clients - Kubernetes -Credentials - Secret.
Make sure to secure copy the rootCA.crt certificate into the path '/etc/kubernetes/pki/' (Look at https://blog.mohammedx.tech/keycloak)
Th JWT token coming from Keycloak will consist of some attributes, these lines tells Kubernetes to retrive the name for the username, groups for the group field from the Kubernetes client in Keycloak.
Now, when a user tries to make API request, Kubernetes will need the authorization token (JWT) as a header (This token consists of the username and in what group the user is).
In our case, when creating a JWT token for the user mohammed using ussername: mohammed and its password, If credentials are correct, the token will identify the user as a JWT token. Next, this token is injected to the API request as an authorization token identifying mohammed as a developer.
However, at this moment, Kubernetes doesn't allow developers to access anything because we didn't make a role and a roleBinding (More about this read RBAC fron Kubernetes documentation).
Let's make a clusterRole that tells Kubernetes to allow users from group developers to access the API server.
nano developersRoles.yaml
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: developer-role
rules:
- apiGroups: [""]
resources: ["namespaces","pods"]
verbs: ["get", "watch", "list"]
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: developer-crb
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: developer-role
subjects:
- kind: Group
name: "developers"
apiGroup: rbac.authorization.k8s.io
kubectl create -f developersRoles.yaml
Now evrything should be set up.
Let's try to access the Kubernetes API without a valid JWT token:
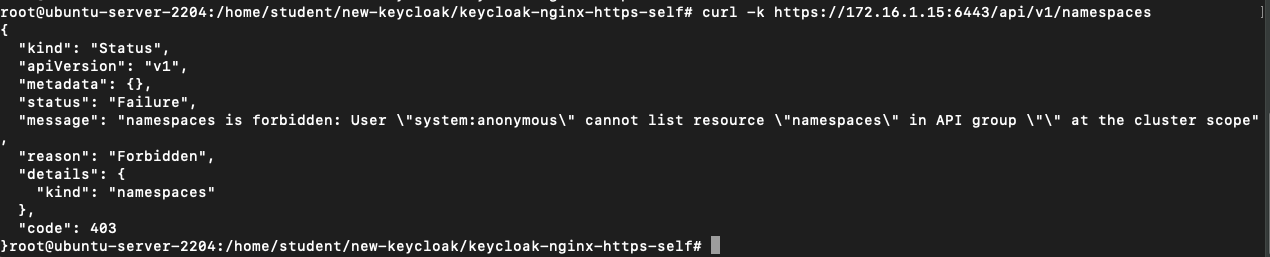
This tells us that to access the API server, we need to generate a valid id_token for a valid user that is a developer in "developers" and inject the JWT token into the request.
First, generate a JWT token for the user mohammed:
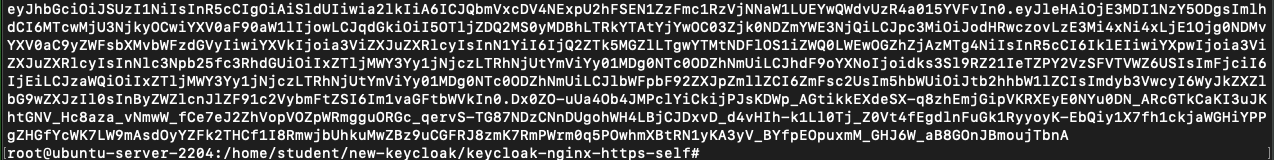
Now add this token into the request using -H
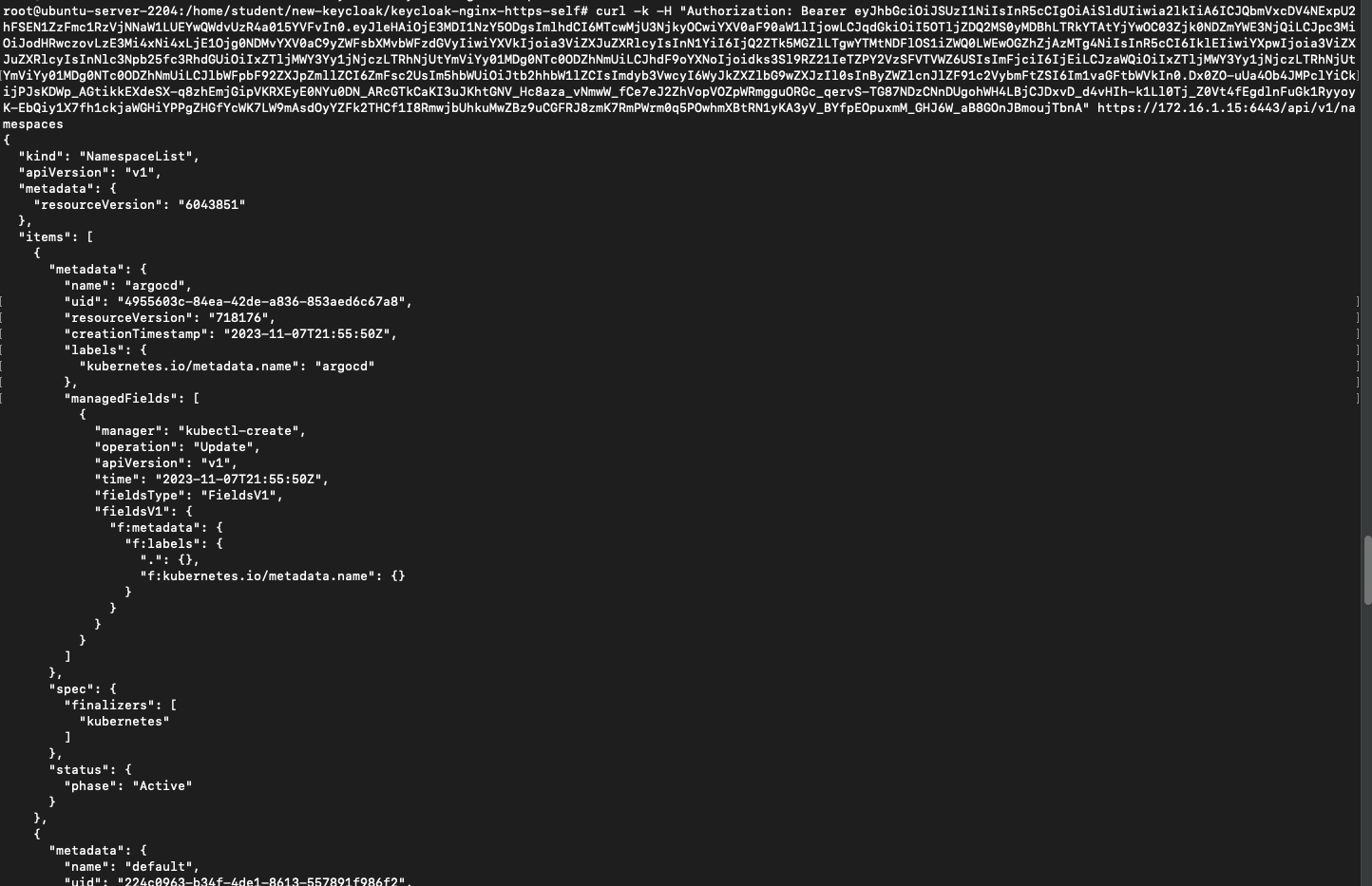
The following section introduces a plugin that streamlines the authorization process. This plugin generates a login page, and upon successful user login, 'kubelogin' automatically obtains the ID token. This facilitates seamless access to the API.
Kubelogin
Kubelogin is a tool that simplifies Kubernetes authentication by integrating with OIDC (OpenID Connect), automatically handling the exchange of credentials and tokens for accessing Kubernetes API services.
Install it from: https://github.com/int128/kubelogin?source=post_page-----eba81710f49b-----------------------------—
Using the following command with replacing variables:
kubectl oidc-login setup \ --oidc-issuer-url=https://<keycloak_server-url>/auth/realms/master \ --oidc-client-id=kubernetes \ --oidc-client-secret=<CLIENT SECRET FROM ABOVE>
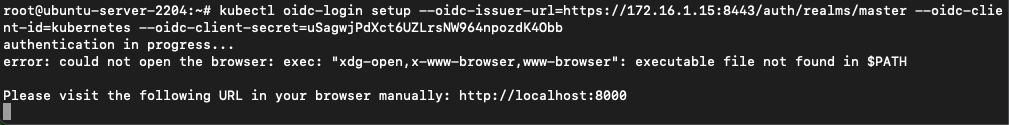
kubelogin will ask the user to open localhost:8000 to login. If the user logs in successfully, kubelogin will automate the process of injecting the id token into the request.
navigating to localhost:8000
Logging in,
kubelogin immediately return the response of my request: